Detect, Prioritize, and Remediate Active AI Risk
Sysdig AI Workload Security helps mitigate Active AI Risk – flagging any suspicious activity or changes to workloads that contain AI packages.
-
Uncover Active AI Risk
Automatically tags the most common AI engines such as OpenAI, Tensorflow, and Anthropic running in your environment prioritized by their risk exposure.
-
Real-time Detection
Detects suspicious activities and threats within AI workloads, such as remote file copy in real time. Stop data leaks before they start.
-
Stay Ahead of Emerging Regulations
New AI regulations are coming. Stay ahead of them by providing clear visibility on what AI workloads you have, where they are, and what risks are associated with them.
Active AI Risk Findings
Enrich static risks, such as public exposure and misconfigurations, with real-time threats and suspicious activities like shell access or remote file copy to help prioritize the most imminent risk to your AI workloads and data.
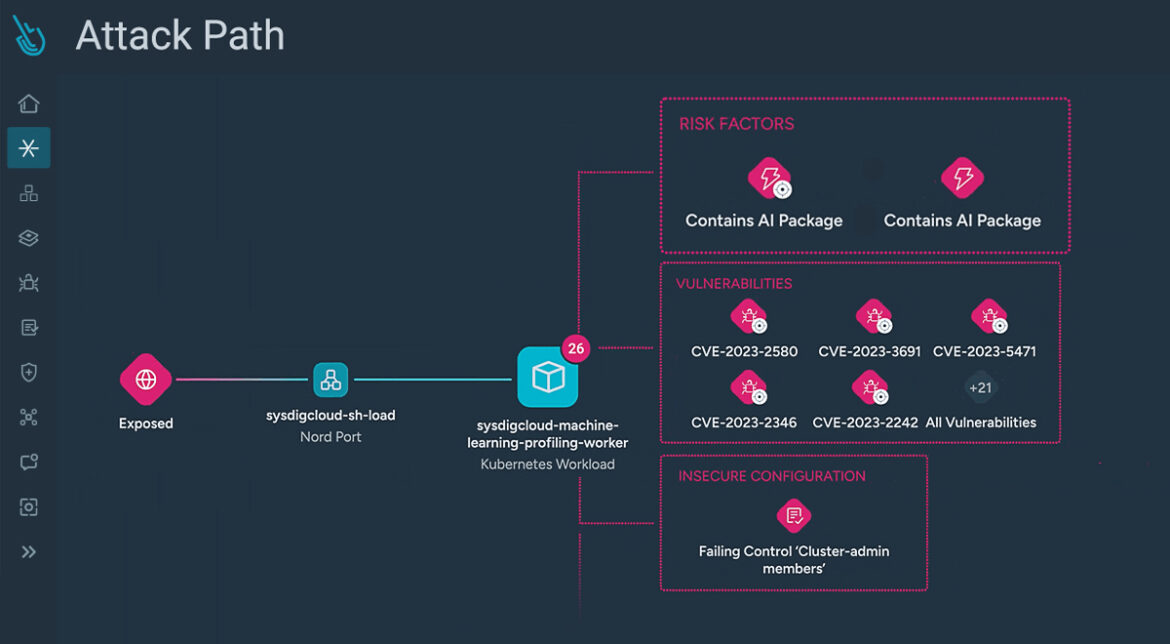
Attack Path Analysis
Uncover hidden attack paths. Correlate AI assets with activity and visualize risks with interconnected resources. With runtime insights, real-time detections reveal active lateral movement, helping you stop attackers in their tracks.
Runtime Vulnerability Exposure
Prioritize critical vulnerabilities in your AI deployments. Leverage runtime insights to identify the in-use AI packages with the highest risks and prioritize the most critical vulnerabilities to fix first.
Secure AI Workloads with Runtime Insights
Combat real-time threats and prioritize active AI risks with runtime insights. Only Sysdig offers:
How fast can you defend against cloud attacks?
Join our next virtual lab to see a real-world cloud attack in action. In 60 minutes, our instructor will show how you detect and respond to a threat in real time.